Note The following are the Stateless Ethereum initiative:
Research Activity (Comprehensively?) The second quarter of 2020 saw a slowdown because all the collaborators have adjusted their lives to this bizarre timeline. But As The ecosystem is getting closer. Serenity The Eth1/Eth2 merge and the work Stateless Ethereum They will be more influential and important. Expect An An even greater year-end stateless is possible Ethereum In The next few weeks will be retrospective
Let’s Please You can read the summary once more: The The ultimate goal is Stateless Ethereum It It is to get rid Requirement An Ethereum Node Keep a copy of your proof-of-state up to date at all times InsteadState changes can be made on the basis of a small amount of data that indicates that a transaction has caused a valid change. Doing This Solves a major problem Ethereum; An issue that has been further exacerbated due to the use of more client software. State Growth.
The Merkle You Will need to provide evidence Stateless Ethereum It It is also known by the name “a” “witness” By It attests to the state change by providing all. Unchanged Intermediate For a new valid state root to be reached, it is necessary that hashes be performed. In In Tokens may be smaller than full-sized coins in theory. Ethereum State They are still synchronized, although it can take up to 6 hours. Even Larger It This is more efficient than a single block and must spread to the entire network in a matter seconds. ThereForeIt It is essential to know the exact dimensions of the tokens to be able to obtain them. Stateless Ethereum To achieve minimum profit.
Much Like The state of Ethereum Smart A large amount of the additional weight (digital) in tokens is due to contract code. If When A transaction must call a contract. The token must include the contract’s default bytecode. In Its Whole With The witness. Code Merkelization This It is a general approach to reducing the burden of smart contracts coded on tokens. Contract Only the code bits are required for calls “touch” You can verify their validity. With This Technique alone could lead to a significant decrease in witness. HoweverThere are many details to consider when breaking down smart contract codes into bite-sized parts.
What Is Is bytecode possible
There There There are certain tradeoffs to be made when splitting a contract bytcode. The The The question that we will eventually have to answer is “how big will the code snippets be?” – but for now, let’s look at actual bytecode in a very simple smart contract, just to understand what it is:
Pragma Solidity >=0.4.22 <0.7.0; Contract Storage { The number uint256; Function Store(Number uint256) Public { Number = Num; } Function Retrieve() Public View returns (uint256){ Return Number; } }
When When This simple storage contract was compiled. It is machine code that can be run “within” EVM. HereYou The storage contract can be viewed as described above, but you will also need to see individual EVM instructions and/or optcodes.
PUSH1 0x80 PUSH1 0x40 MSTORE CALLVALUE DUP1 ISZERO PUSH1 0xF JUMPI PUSH1 0x0 DUP1 REVERT JUMPDEST POP PUSH1 0x4 CALLDATASIZE LT PUSH1 0x32 JUMPI PUSH1 0x0 CALLDATALOAD PUSH1 0xE0 SHR DUP1 PUSH4 0x2E64CEC1 EQ PUSH1 0x37 JUMPI DUP1 PUSH4 0x6057361D EQ PUSH1 0x53 JUMPI JUMPDEST PUSH1 0x0 DUP1 REVERT JUMPDEST PUSH1 0x3D PUSH1 0x7E JUMP JUMPDEST PUSH1 0x40 MLOAD DUP1 DUP3 DUP2 MSTORE PUSH1 0x20 ADD SWAP2 POP POP PUSH1 0x40 MLOAD DUP1 SWAP2 SUB SWAP1 RETURN JUMPDEST PUSH1 0x7C PUSH1 0x4 DUP1 CALLDATASIZE SUB PUSH1 0x20 DUP2 LT ISZERO PUSH1 0x67 JUMPI PUSH1 0x0 DUP1 REVERT JUMPDEST DUP2 ADD SWAP1 DUP1 DUP1 CALLDATALOAD SWAP1 PUSH1 0x20 ADD SWAP1 SWAP3 SWAP2 SWAP1 POP POP POP PUSH1 0x87 JUMP JUMPDEST STOP JUMPDEST PUSH1 0x0 DUP1 SLOAD SWAP1 POP SWAP1 JUMP JUMPDEST DUP1 PUSH1 0x0 DUP2 SWAP1 SSTORE POP POP JUMP INVALID LOG2 PUSH5 0x6970667358 0x22 SLT KECCAK256 DUP13 PUSH7 0x1368BFFE1FF61A 0x29 0x4C CALLER 0x1F 0x5C DUP8 PUSH18 0xA3F10C9539C716CF2DF6E04FC192E3906473 PUSH16 0x6C634300060600330000000000000000
As This This is how it works a previous postThese The core operations of EVM stack architecture are represented by opcode commands. They Define The storage contract with all its functions. You This Contract is an example of a robustness agreement in the Remix IDE (Note The An example storage is machine code. Once It is in placeNot The output of Solidity compiler that will contain some additional opcodes (“boot”) If You can imagine a physical stacker performing step-by–step calculations on opcode card. The The blurring caused by the moving stack makes it almost impossible to see the functions. Solidity contract.
Every When When the contract is called, this code will then be executed within each Ethereum Validating Nodes for adding new blocks to your network To Send A valid transaction Ethereum You You will need a copy of the contract-bytecode today. Running You must follow the code from beginning to ending in order to obtain the exit status (deterministic), and associated hash.
Stateless EthereumRememberThe goal is to alter this requirement. Let’s All You just need to dial the function Retrieve() And There is nothing more. The The The logic that describes the function of a contract is just one subset. In The EVM does not require any of these functions in this example. The Basic blocks Opcode Statement To return the value you desire
PUSH1 0x0 DUP1 Swap1 POP SWAP1WUMP JUMPDEST DUP1 DUP3 DUP2 POPS1: 0x20 ADD SWAP2 PUS1: 0x20 POPS1: 0x40 DUP1 SWAP2 DUP2 SUBSWAP1 RETURN
In The Stateless paradigm requires that the token provide missing ishes for an untouched state. Tokens must also contain missing hashes that allow for the execution of unexecuted machine code. Which This is the current running. .
The Witness code
Smart Contracts Ethereum Live In the same spot externally-owned accounts are: as leaf nosdes within the single root state trioe. Contracts They They are very similar to accounts that are owned externally. They Have An address is required to send transactions. Ether These You can also use tokens. But Contract Accounts are unique because they require their own program logic (code), or a hash. Another Associate Merkle-Patricia TrieThe The aforementioned is also known by the StorageTrie Permanent Variables are saved to allow active contracts to continue their business operations during execution.
This visualization of tokens provides a good idea of how important commercialization of the code could be in reducing the size of the tokens. See This A huge chunk of colored pieces is larger than all the other elements of the trie. That’s One chunk of smart contractbytecode
Next The The lingering status pieces are slightly less than the average. StorageTrieERC20 digital item ownership manifests and ERC721 balance assignments Since This This is an example token. It is not a complete snapshot of the state. These They are also mostly composed of intermediate hashes. They Only contain the changes that a client who is not a stateless would require to test the next blocks.
Code Merkleization It is a method that allows you to break down large blocks of code and then replace them with a field. Hashcode into an Ethereum Account with the root Merkle TrieThe Named appropriately Codetrie.
Worth Its Weight in hash
Let’s Take Take a look at this illustration This Video is from Ethereum Engineering GroupThis This article examines different methods of code fragmentation using an A. ERC20 Sheet contract. Since Many Most tokens you’ve seen conform to the ERC-20 standard. This This provides an actual-world context to understand codemerkleization.
Since The The bytecode is messy and long. Let’s Quickhand: Replace four bytes (8 hexadecimal characters) with a . Either X character and the latter represent byte codes for execution of a function (in our case, the ERC20.transfer() This You can use function in all situations.
In The ERC20 example calls Transfer() The It is less efficient because the entire smart contract serves a function.
XXX.XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX.......................................... .....................XXXXXX..................................... ............XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX........................................ ........................XXX.................................XX.. ......................................................XXXXXXXXXX XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX...............XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX.................................. .......................................................XXXXXXXXX XXXXXXXXXXXXXXXXXXXXXXXXXXXXX..................................X XXXXXXXX........................................................ ....
If We I wanted to convert that code into 64-byte chunks. It It would only take 19 of 41 pieces to execute stateless codes. Transfer() TransactionThe remaining data is from a witness.
|XXX.XXXXXXXXXXXX|XXXXXX..........|................|................ |................|.....XXXXXX.....|................|................ |............XXXX|XXXXXXXXXX........|................|................ |................|........XXX.....|................|............XX.. |................|................|................|......XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX |XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX|XX..............|.XXXXXXXXXXXXXXX|XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX |XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX|XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX..|................|................ |................|................|................|.......XXXXXXXXX |XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX|XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX...|................|...............X |XXXXXXXXXXX........|................|................|................ |....
Compare This This is 31 out 81 chunks within 32-byte chunking systems.
|XXX.XXXX|XXXXXXXXXX|XXXXXX..|........|........|........|........|........ |........|........|.....XXX|XXX.....|........|........|........|........ |........|....XXXX|XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX|........|........|........|........|........ |........|........|........|XXX.....|........|........|........|....XX.. |........|........|........|........|........|........|......XX|XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX |XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX|XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX|XX......|........|.XXXXXXX|XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX|XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX|XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX |XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX|XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX|XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX|XXXXXX..|........|........|........|........ |........|........|........|........|........|........|.......X|XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX |XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX|XXXXXXXXX|XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX|XXXXX...|........|........|........|.......X |XXXXXXXXXX|........|........|........|........|........|........|........ |....
On On On the surface, it appears that smaller pieces perform better than larger ones. Most empty Less Chunks are common. But Here We should also remember that unutilized codes come with a cost: Every unexecuted code line is automatically replaced by a hash Fixed Size. Smaller Code Code fragments called snippets contain code fragments that have more hashes of code than are used. These Hashes can be as large as 32 bytes or as small as 8 bytes each. At You This point might be the best! “Wait! If the hash of the code snippets is a standard size of 32 bytes, how would replacing 32 bytes of code with 32 bytes of hash help?”
Remember The The contract code is merkleizedAll The hashes in the resulting codes are linked. Codetrie — The We need root hash to validate the block. In This Any purpose can be served by structure Sequential Unexecuted No matter how many there are, shards only require one hash. That This A hash could also be used to denote a large number of sequential hashes. Merkleized CodeSo long as they are not needed for the encrypted execution
We Additional Data must be gathered
The The We have come to the following conclusion: it is not a climactic conclusion. “optimal” scheme for code merkleization. Layout Options You can reduce the size of snippets or add them to hashes. You Data from the’real’ world can be relied upon. Each Smart Contract trades are different so researchers need to determine which format is most effective for monitoring mainnet activity. What What What does this actually mean?
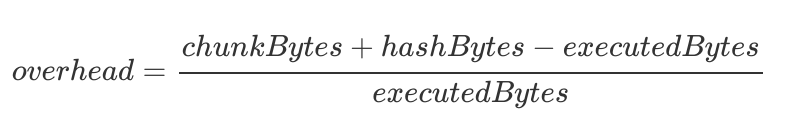
One One One thing that could indicate efficiency in a code merkleization programme is Merkleization OverloadWhich Answer the following question “how much additional information beyond the executed code is included in this token?”
We You can find it here Some Promised resultsCollect Use A tool designed specifically for you Developed By Horacio Mijail From The Consensys TeamX Research TeamShow overheads as low 25% Not bad!
In In Summary: The data suggests that smaller chunks work better than larger chunks, especially if smaller (8 byte) hashes are used. But These The early numbers don’t represent all blocks and there are only 100 available. If If You are reading this and would like to contribute. Stateless Ethereum You You can take the initiative to gather more code merkleization information. Please Introduce yourself on the Eth1x/research Discord Oder on the ethersear.ch forums. two!
And As We are always available to answer questions, comments, or other requests. “The 1.X Files” And Stateless EthereumSend Send a message to @gichiba, or send an email directly. Twitter.

